DIGITAL FORENSICS
End to End DFIR Services and Solutions
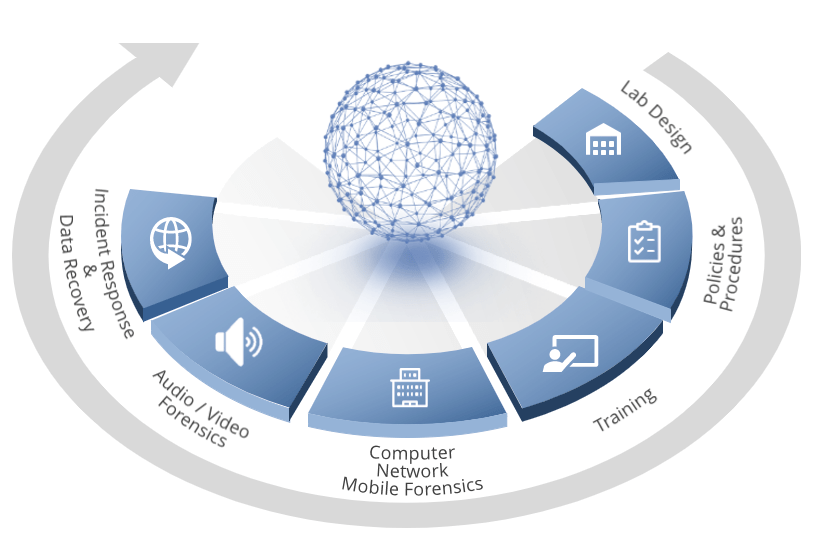
AGT DFIR Methodology
When setting up and deploying a Digital Forensics Lab, there are many factors that need to be taken into account and many bases that have to be covered. AGT’s methodology offers a comprehensive approach to ensure that your Digital Forensics Lab and your team have everything they need. First, we equip the lab with the very latest state-of-the-art digital forensics solutions, then through a comprehensive training program we ensure that you are able to develop a highly qualified professional team of digital forensics examiners, and finally we ensure the continuation of modulated growth of your digital forensics’ capability, infrastructure, policies, procedures and efficiency to a level that would facilitate successful ISO/ASCLD certification.
Our approach is to carry out an improvement and implementation process that allows you to:
- Effectively operate a Computer Forensics and Media Recovery Capability with the most advanced and cutting-edge technologies
- Improve the investigation and analysis methodologies, to achieve the highest global standards
- Gain the knowledge via our mindful tutelage to be able to successfully operate on your own
To achieve these goals, we will be by your side providing you all the support you will need in all the phases of the project:

- Analysis: we will carry out an analysis of your current capabilities and your forensics needs, and we will design the best possible solution for your specific case.
- Implementation: we will provide all the necessary equipment, as defined in the Design, and we will put it together in an optimized deployment. We will also define and develop all the processes, procedures, documentation and everything else that you need to operate your laboratory efficiently over time, making sure that your cases get to Court with the maximum guarantees of success.
- Training: Many different methods and processes are involved in digital forensics investigations. In order to improve the process of gathering and analysing data, a great deal of knowledge is required regarding how data is stored and processed. Our training program is designed to ensure that all students develop a firm grasp of the knowledge, processes and methods required for digital forensics investigations.
- Support: we will provide you 3rd level support with any questions you may have or any other support you may need during the daily operations. We will update you about the new available technologies, the most recent advances in Computer Forensics, and anything else you need to know. You will not only have at your hand the vast knowledge of our Forensics experts, but also the possibility to reach the top experts globally in this field also.
- Provisioning: we will ensure that your equipment and supplies are up-to-date, adding new tools that will boost the performance of your scarcest resource: your investigators. Investing in the right tools and techniques will save you time and money.
Forensic Hardware
Our forensic hardware is designed with investigators in mind, and features award-winning technology and top-of-the-range computer processors. The hardware is engineered to be high-performance, to have reduced noise emissions and to feature sustained system cooling. The products that we offer include:
Forensic Imaging

Our forensic drive imaging and write-blocking devices create disk clones and manage images, as well as log and maintain your chain of custody, while using forensic write-blocked methods. These devices offer advanced, high-performance forensic imaging at unbeatable speeds. Designed for use both in the field and in forensic labs and engineered specifically for investigators, the forensic imager features a compact footprint and user-friendly navigation.
Computer Forensics

Computer forensics involves acquiring, retrieving and analysing data found in computers and proving that the evidence provided is true. The process also allows you to determine whether an additional enquiry is warranted by quickly finding, recognising and prioritising possible evidence in computers. This will cause a reduced backlog, so that investigators can focus on getting a case closed.
Mobile Forensics

Mobile forensics involves the capture and analysis of data, through logical or physical acquisition of the mobile device. We offer the tools and know-how to access a wealth of information that has been extracted from a constantly evolving range of smartphones.
Video Forensics

Video forensics is a group of multimedia analysis and clarification software tools for video, audio and images, which offers a well-organised and seamless workflow for both novices and adept forensic video specialists and audio experts. It also offers extensive video, image and audio analysis and processing capabilities.
Audio Forensics

Audio forensics provides a highly accurate voice identification tool to forensic experts to support criminal investigations. For automatic identification of the speaker, the latest voice biometric algorithms are used.
Network forensics

Network forensics runs real-time threat investigations to spot any kind of data leakage or instructions to examine network traffic to recognise trends and gather intelligence.
Password Recovery

Password recovery tools allow governmental and corporate clients to unlock disks and systems, as well as decode files and documents protected with other widely known applications. By encrypting file systems, Windows and email accounts, password recovery enables the user to recover passwords to a variety of office documents and archives, and remove many other kinds of password protection.
Faraday Bag

The faraday bag is used to ensure that mobile phones cannot be connected to remotely, preventing remote hacking, remote wiping of data or evidence and remote surveillance. This bag can be used for mobile phones, GPS and other similar-sized devices.
JTAG & Chip-Off Solutions

In this advanced digital data extraction and analysis technique, flash memory chips are physically removed from a subject device and then raw data is attained, using specialised equipment.
Case Management

Case management is a solution for managing digital forensic cases and investigations. It allows investigators to manage their cases using a single, centralised platform that is designed to manage and track cases, reports and findings with its programmed case workflow management.
Mobile Car First Responder

The mobile car first responder is a mobile lab that is equipped with various forensic hardware and software tools, for use in conducting an investigation.


